HOME > Database Services > Oracle Database Vulnerability Assessment Service
Oracle Database Vulnerability Assessment Service
The Current State of Database Security Measures
Despite knowing the importance of database security, many companies still do not have any security measures in place.

Some of the obstacles getting in the way of database security measures are:
- • Higher priority given to network perimeter defense
- • Uneven application support
- • The cost and difficulty of using security products
- • Lack of clarity on which department should pay for security products
The general sentiment in the workplace is that even though database security is clearly important, no one can move forward with plans to address it.
We believe that both top-down (management-driven) and bottom-up (IT-driven) approaches to the problem are important.
In recent years, most security incidents have been caused by either external attackers who exploit web application vulnerabilities or internal attackers who access a company's databases directly. In fact, domestic Japanese companies need stronger database security to address the large number of incidents that have been caused by insiders acting illegally.
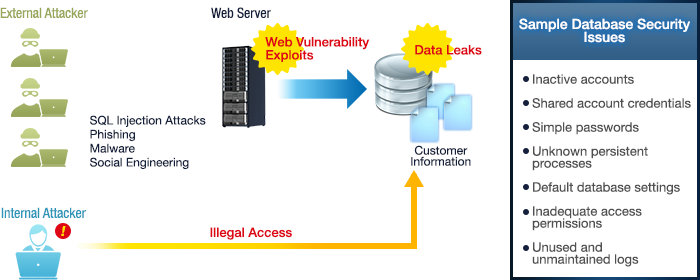
We recommend database assessments to our clients so that we can better understand their situations and create milestones for database security measures.
Characteristics of an Oracle Database Vulnerability Assessment
- Examine and propose security requirements
We examine and propose security requirements for each client given their particular circumstances, the problems they face, and the properties of their IT systems. - Conduct a detailed database assessment
We check dozens of database properties informed by our experience building and running database systems. - Present concrete proposals for enacting security measures
We consider and present concrete steps to address the issues we identified in our assessment report. - Integrate with database (performance) assessments and tuning services
We provide a smooth transition to our tuning services after security measures have been enacted.
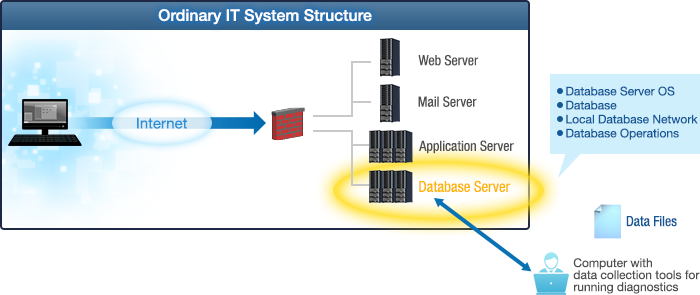
System Components Covered by a Vulnerability Assessment
How We Conduct Vulnerability Assessments
- • We use a computer provided by the client to access the databases we are assessing.
- • We create a user (schema) on the database we are assessing.
- We configure access permissions for this user and delete it when we are done.
- If we are unable to create this user (schema), we cannot determine which security patches have been applied but we can perform other basic diagnostics. - • We use email or external media to bring the results of our assessment back to our office for further analysis. If this turns out to be difficult, we can also analyze the data onsite at the client's office.
Vulnerability Assessment Flowchart
 |
 |
 |
 |
|---|---|---|---|
| Interview topics: - Current issues - Current setup and settings - Client security policies - Operational methods - Future system updates • Methods for gathering data to analyze • Assessment schedule • Target and scope of the assessment • Available configuration data |
• Configure information-gathering tools • Information to collect: - Network structure and settings - Operating system settings - Log configuration management - Database information • Permissions • Accounts • Settings and applied patches |
• Current conditions to report: - Basic database assessment metrics - Issues • Discuss proposed improvements to address the results of the assessment and current issues experienced by the client • Security requirements to consider: - Data attributes - System attributes - Basic assessment metrics - Current issues |
Proposals to present and discuss: - Database modifications - Structural system modifications |
 |
 |
 |
 |
Vulnerability Assessment Options
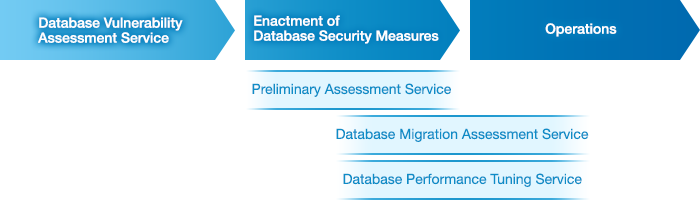
- In our preliminary assessment service, we check the behavior of test systems and examine their performance before incorporating new security products and/or functionality. (Note that under some circumstances we may be unable to offer a preliminary assessment.)
- In our database migration assessment service, we analyze database performance after security measures have been enacted (after new security products and/or functionality have been incorporated); we also present a list of issues and proposed countermeasures.
- In our database performance tuning service, we address database performance issues after security measures have been enacted by conducting instance, parameter, and SQL tuning.

Database Services TOP
- Re:Q's Advantage on Database Services
- Oracle Database Assessment Services
- Oracle Database Design and Implementation Services
- Oracle Exadata Services
- Oracle Database Administrative Support Services
- Oracle Database Migration and Disaster Recovery Services
- Oracle Database Vulnerability Assessment Service
- Re:Database Services


